As more and more powerful smart mobile devices available in the market, most enterprise CIO’s face an inevitable challenge: how to position the role of personal mobile device in enterprise IT environment. At this moment, your smart phone or tablet can provide better functionality and performance than your laptop can do: checking out email, reading document, filling in commercial form, accessing data from privileged enterprise resources…etc. There are lots of advantages to have such personal device work in enterprise IT environment, but there are also lots of risks behind.
 The trend – Bring Your Own Device (BYOD) has a great impact on enterprise IT management. BYOD policy will definitely increase the morale of employees, because it can help employees to access both business and private data simultaneously without limit of place, office or home, and time, working hours or off working hours, if network is available. Employees can manage their time efficiently and flexibly to balance private and business lives. That’s so called “ubiquitous” computing environment. On the other hand, there are several concerns of IT security issue behind this trend. The trend – Bring Your Own Device (BYOD) has a great impact on enterprise IT management. BYOD policy will definitely increase the morale of employees, because it can help employees to access both business and private data simultaneously without limit of place, office or home, and time, working hours or off working hours, if network is available. Employees can manage their time efficiently and flexibly to balance private and business lives. That’s so called “ubiquitous” computing environment. On the other hand, there are several concerns of IT security issue behind this trend.
The first concern is the security of personal mobile. There are 2 major issues under this concern: one is data security in mobile device, and the other is physical security of device. Most of mobile devices come without better data protection mechanism, because those are originally designed for consumer use instead of business purpose. Sometimes, privileged data may be lost or stolen through Bluetooth or MicroSD card shift. The other is the problem of mobile device lost. We can see hundreds of mobile devices in the Lost and Found of Airport or Station every day. Even when you sent your mobile device repair, you may still risk of data lost.
The second one is the security of network access. Most enterprises adopt different kinds of security mechanism to control network access from mobile devices. Such mechanism usually causes some inconvenience for end users while logging into enterprise network by mobile devices. Unfortunately, there are several free Apps called “Jail Breaking”, which can find the back door of such security mechanism and make life much easier for end users. So, it will cause a serious internal issue of IT security by this phenomenon.
The other one is the security mechanism in data transmission level. Mobile device usually links with backend systems through WiFi, 3G and 4G networks. The confidentiality and privacy of data transmission is the major concern for CISO or CIO through public networks. If this requirement of data transmission can be can fully controlled by CIO or CISO, mobile device can be easily accepted. In reality, there is still lot of grey area and uncertainty in this field. So, it is hard to tell whether the use of mobile device can be trustful with security mechanism in data transmission.
However, the adoption of BYOD, especially mobile devices, policy is a strong trend inside enterprise. It is not the question of “Yes” or “No”, and it is the question of how much risk of IT security issue your company can afford. IT security mechanism should be adapted to such trend, if there is a better way to keep those IT security issues under strictly control.
“We believe that it is a better strategy to monitor all network traffic from the core switch by certain criteria” said Casper Chang, CEO of Decision Group “in order to check the behavior pattern of network users in LAN.” By this way, any abnormal activities inside network or irregular traffic can be easily sorted out and restricted by instant alarm mechanism.
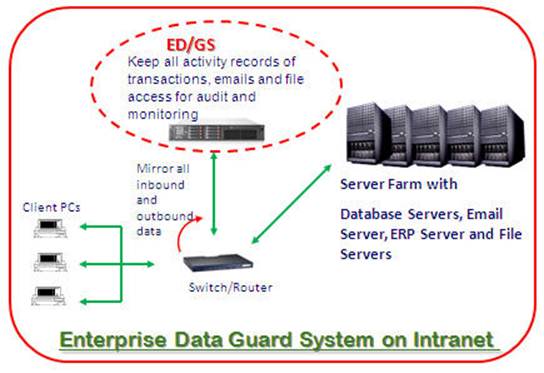
Both E-Detective (ED) and Enterprise Data Guard System (EDGS) can work together against threats from Internet and intranet. ED, deployed against external threats, can monitor all outbound and inbound traffic and find out abnormal activities inside LAN with timestamp, source IP address, content of service, activities…etc. EDGS, deployed against internal threats, can monitor all SQL commands, portal access, corporate mail, file access of file servers, and centralized Skype management…etc. By the security mechanism provided by both ED and EDGS, IT security can be maintained to highest level even though there are lots of accesses from mobile device inside enterprise network.
With advanced DCC (Deep Content Capture) technology, ED and EDGS can capture network traffic, decode those data packets, reconstruct those back to original content based on protocol format, and save all data into database and related files. CIO or CISO can set up keyword or register confidential file in both system for real time security alert and file tracking inside network. On the other hand, CIO or CISO can also conduct data analysis for network behavior analysis in order to prevent from internal threats by disgruntled employees. Regular reports from ED and EDGS can be compliance part of corporate IT security management.
Both multiple ED and EDGS systems can be deployed by distributed way with centralized management system and data retention management system, especially for those global companies or multi-branch companies, such as banks, manufacturers. Lots of companies also benefit from deployment of both ED and EDGS under BOYD policy.
About Decision Group
Decision Group, established in 1986, is one of the leaders in manufacturing of PC-Based Multi-Port RS232/422/425 Serial Cards, Data Acquisition, Measurement Products, Industrial Automation and Control Systems. Decision Group, from the year 2000, started new line of industry involved in designing and development of equipment and software for Internet Content Surveillance and Forensics Analysis Solutions.
Decision Group also provides OEM/ODM services of its deep packet inspection (DPI) technology and solution to other partners worldwide. Decision Group has also developed a comprehensive training course, known as Network Packet Forensics Analysis Training (NPFAT), and has set up training centers worldwide for hands-on real scenario training, with certification option as well.
More Information and Contact by Email: decision@decision.com.tw
URL: www.edecision4u.com (Global), www.internet-recordor.com.tw (Taiwan), www.god-eyes.cn (China), www.decisionjapan.com (Japan) , www.decision-groups.com (Singapore), www.e-detective.de (Germany), www.edecision4u.fr (France), www.edecision4u.es (Spain and Latin America) |